
Let’s recognize it—cybersecurity isn’t just an IT issue anymore; it’s a shared duty for everyone. As we approach 2025, the dangers are higher than ever before. Cybercriminals are growing more sophisticated, tactics are evolving, and the digital landscape is shifting rapidly. How can we keep up to date? From the rise of AI-powered attacks to the vulnerabilities brought about by remote work, let’s investigate the evolving threats in cybersecurity and analyze everything from a consultant’s perspective. Cybersecurity is akin to an intense game of chess—always predicting your opponent’s upcoming strategy. As cybercriminals grow increasingly bold and technology advances, both organizations and individuals are facing a tough battle. The threats have risen not just in number but also in creativity. However, have no fear; this article will help you address the challenges and stay prepared for what comes next.
Current Cybersecurity Landscape
If you believe the cybersecurity landscape is intricate today, just wait to see what will influence it in 2025. Cybersecurity is a rapidly evolving area, and these trends are leading the discussion.
Here are the main factors influencing changes today.
Emergence of AI-Powered Cyberattacks: Picture a hacker who stays alert around the clock and adapts to each action you take. Frightening, isn’t it? That’s artificial intelligence utilized by cybercriminals. Automated assaults are quicker, more intelligent, and more challenging to identify, compelling companies to reconsider their defense strategies. AI-driven phishing schemes and malware are merely the surface of the issue.
Rising Significance of Zero Trust Architecture: “Always verify, never trust”—this is the principle steering Zero Trust Architecture. Organizations are moving away from perimeter-based security towards a comprehensive strategy where no one, whether internal or external, is trusted without proper verification. This is now essential as everything becomes highly interconnected.
How Telecommuting Reshapes Cyber Threats: Recall the time when home-based work seemed groundbreaking? It arrived with significant conditions attached.
The Function of Shadow IT: Workers enjoy utilizing personal apps and tools to increase efficiency, but numerous ones are unchecked and pose risks. This “shadow IT” generates blind spots that render companies susceptible to assaults.
Challenges of Endpoint Security: Each laptop, smartphone, and tablet utilized by remote workers represents a possible access point for hackers. Protecting endpoints has emerged as a top priority, yet it continues to be a challenging endeavor.
Developing Cyber Threats

So, what are the latest “boogeymen” that cybersecurity professionals are worrying about? Let’s examine it.
Ransomware Development: Ransomware remains prevalent; it’s simply becoming increasingly advanced. Currently, assailants are not only encrypting data but also releasing it if their requests go unanswered. This trend of double extortion has companies treading carefully.
Refined Phishing Techniques: Modern phishing emails no longer shout “spam.” They are cleverer, tailored, and persuasive enough to deceive even experienced experts. Attackers are imitating actual people and organizations, which complicates the detection of warning signs.
Cloud Vulnerabilities Increasing Dramatically: The cloud is adored by many—for all the incorrect reasons. Although it’s beneficial for scalability, shared environments imply that if a single door is ajar, it may be taken advantage of.
Misconfigurations: The Quiet Threat: Dismiss complex breaches; even a minor cloud misconfiguration can lead to significant chaos. Basic mistakes in configuring cloud resources render organizations vulnerable.
Third-Party Threats in Cloud Environments: The security of your cloud provider is integral to your own security. A fragile connection in the chain, such as a third-party partner, can lead you into a breach more swiftly than you realize.
The Human Factor
Weakest Connection or Initial Defense Line? Technology can only get you to a certain point. The human factor has a significant impact on cybersecurity—either positively or negatively.
Employee Education and Training: An informed staff member is your strongest line of defense. Ongoing training in recognizing phishing attempts, secure browsing habits, and other best practices significantly aids in avoiding incidents.
Insider Threats: Deliberate or Unintentional: Not all insider threats stem from malicious intent. Occasionally, an employee might mistakenly click on an incorrect link or upload information to the wrong server. However, regardless of intent, insiders present a risk that cannot be ignored.
Role of Cybersecurity Advisors
Curious about how cybersecurity consultants play a role in this picture? They’re your hidden advantage in maintaining an upper hand against dangers.
Recognizing New Threat Paths: Consultants provide a new perspective on your systems, revealing dangers you were unaware of. Their skill in identifying the newest vulnerabilities ensures you stay ahead.
Creating Robust Strategies: Consider consultants as the architects of your digital security stronghold. They develop complex strategies customized to your distinct environment, making certain you’re prepared for whatever attacks hackers may launch at you.
Effective Strategies for Staying Safe
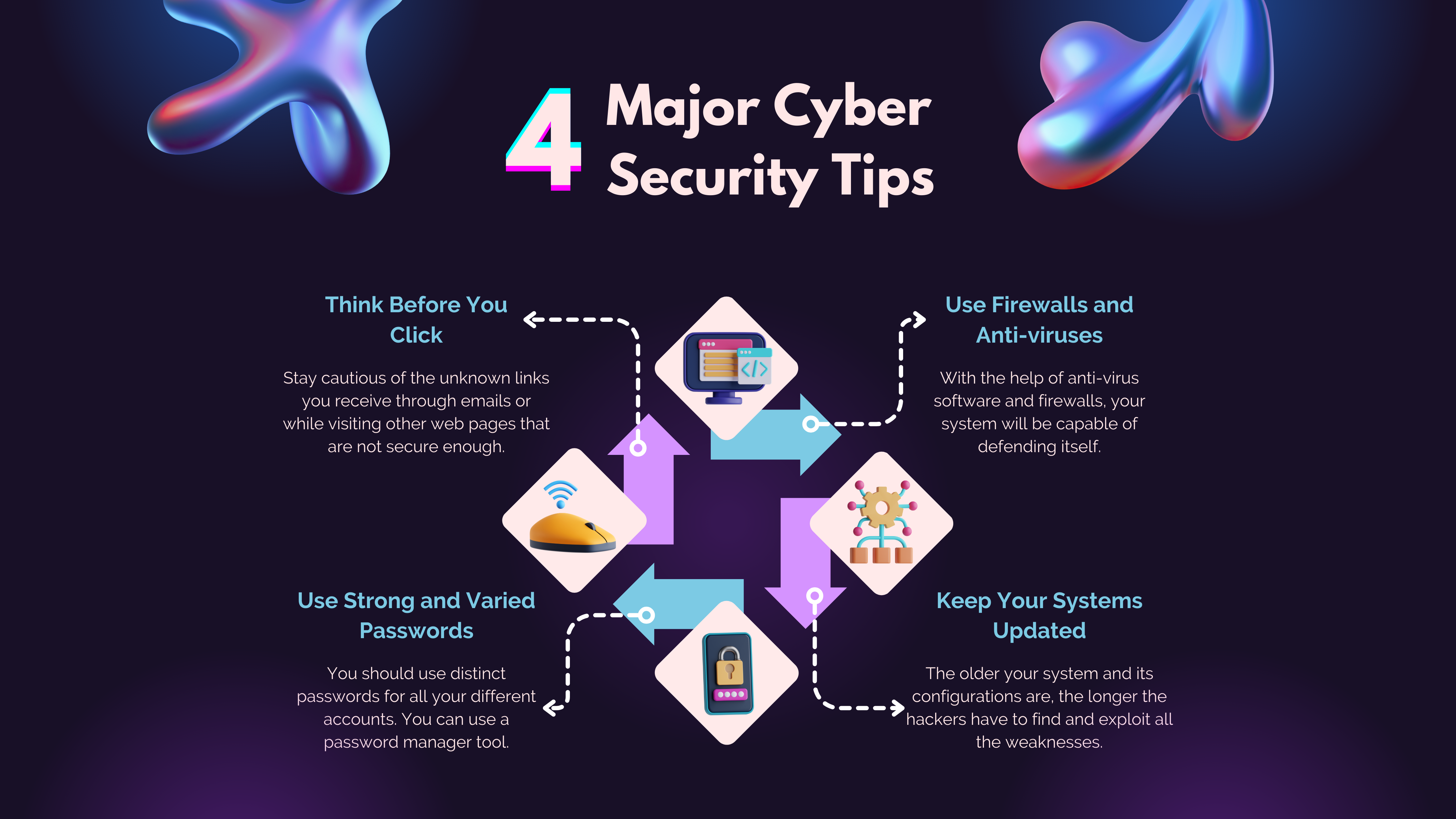
Stay calm. By employing effective strategies, you can greatly reduce your risk. Here are several actionable steps you can implement today.
Multilayered Cybersecurity Strategies: The era of depending on just one antivirus software is over. Employ various defenses such as firewalls, intrusion detection systems, and endpoint security tools for strong protection.
Adopting Proactive Threat Intelligence: Responding to threats after they occur is a futile strategy. Rather, take initiative: observe trends, analyze attack patterns, and remain a step ahead. Instruments such as SIEM (Security Information and Event Management) are revolutionary.
Routine Incident Response Drills: Repetition leads to mastery. Conduct simulations of possible cyberattacks with your team to uncover weaknesses in your response strategy. Believe us; this is a game changer.
Conclusion
At this point, it is evident: cybersecurity demands a combination of awareness, technology, and training. The dangers are changing, and so are our protective measures. By adopting the right mindset, engaging in strategic planning, and fostering collaboration, you can protect your organization from even the most sophisticated attacks. Therefore, what is the main point to remember? Don’t merely respond to threats—foresee them. Let’s turn 2025 into the year we outwit cybercriminals in their own arena.
Published: December 11, 2024







